
Over the last decade, airports have made a tremendous leap into the evolving age of technology. User-friendly airline and airport websites, online check-in, unmanned border controls, automated checked baggage systems, Wi-Fi networks, the list goes on. However, networked hyper-connectivity exposes us to cyber-threats. And just as technology rapidly evolves, cyber-threats are doing so too. Monika Simonaityte reports.
Cyber-security incidents are dramatically increasing year-on-year across the full spectrum of international trade. Due to their visibility, disruption of the essential operations of airlines and airports could feasibly be the subject of a cyber-attack by cyber terrorists.
One such example would be the attack on Istanbul Atatürk and Sabiha Gökçen airports. In July 2013 the passport control systems at the departure terminals in both of these airports were shutdown by a cyber-attack. Passengers were forced to stand in line for hours, and the majority of flights were delayed. Even though the systems were restored, the damage could be felt for many hours after.
In order to keep the global aviation system operating smoothly, the industry relies on information and communications technology (ICT) to deliver critical information, empowering the people working within the network. It is clear that airport infrastructure supports many different operations that are critical for the efficiency and effectiveness of the air transport system.
Unfortunately, not all airports have implemented cyber-security systems that would protect and control those operations and all related features. It simply means that even though many may have security measures in place, cyber criminals, ‘hacktivists’, or cyber terrorists may consider this as a perfect opportunity to attack the airports in many different ways.
4 types of security incident
But first, we need to understand what are the possible threats for airports. According to 9 Steps to Cybersecurity by Dejan Kosutic, there are four types of security incident: Natural Disaster, Malicious Attack (External Source), Internal Attack, and Malfunction and Unintentional Human Error.
Firstly, natural disasters – these include severe floods, earthquakes, snow, and ice storms, hurricanes and other hazardous natural processes that may disturb the business continuity of an airport or even completely shut down the airports for an indefinite amount of time.
Secondly, malicious attacks are a serious threat, which usually come from external sources. These attacks are taking place all around the world almost every minute and the targets vary from banking systems to e-mail servers. In terms of airports, the most ‘desirable’ exposed parts could be public wireless hotspots, which are heavily used by the passengers at almost every airport; the baggage systems, serving thousands of passengers’ belongings; main airport websites, and so on.
Thirdly, if a member of the airport staff destroys airport data, leaks sensitive information, or in a worst-case scenario, harms the systems intentionally, then the airport would not have a pleasant experience from an internal attack.
And finally, sometimes the airport may suffer from random errors or accidental failures like power loss, equipment shutdown or damage, loss of internet and phone lines; this type of incident would be called a malfunction and unintentional human error.
As mentioned, the air transport industry is one of the targets likely to be selected by cyber terrorists, be it airlines or airports.
It is crucial to understand that the disruption caused by a cyber-attack also depends on the airport’s size and traffic. However, all these types of incidents may result in long-term implications for any type of the airport.
Loss of operations for any period of time would seriously harm the business. The same goes for reduced throughput of, for example, Hold Baggage Systems, which would lead to chaos from the passenger’s side, and operational productivity would drastically drop.
Moreover, the leakage or destruction of data does not sound convincing – sensitive information may reach third parties that are waiting to use it for their own interest, which could be disastrous not only for the airport, but also for the whole of the aviation sector.
Usually, any severe incidents that require time to be solved inevitably lead to a financial loss; whether it affects a stable hub airport or a small regional airport, delays or cancellation of flights result in high recovery costs.
If that were not worrying enough though, the whole situation would be aggravated by the press and an immediate negative ripple effect on social media.
According to 9 Steps to Cybersecurity by Dejan Kosutic, there are four types of security incident: Natural Disaster, Malicious Attack (External Source), Internal Attack, and Malfunction and Unintentional Human Error.
Preparing for the worst
That’s not to say that airports will be left entirely defenceless against this new foe; there are many activities ongoing in Europe from different institutions and bodies aiming at spreading awareness of cyber-attacks and how to protect businesses. In 2013, the European Commission released a policy document called Cybersecurity Strategy of the European Union: An Open, Safe and Secure Cyberspace that invites industries to take certain actions at the national level in order to protect their business and to have harmonised cyber-security measures among all Member State airports in the EU.
In early 2014, the EU Cyber-security strategy was reviewed and it was agreed to continue the work with the Member States, national and private organisations.
The European Commission has also developed a policy on Network and Information Security (NIS). The aim of this policy is to better coordinate cyber-security measures between EU institutions and EU Member States, involving public and private sector cooperation. The European Network and Information Security Agency (ENISA) was established in 2004 and a new Regulation to strengthen ENISA and modernise its mandate is currently being negotiated by the Council and European Parliament.
Despite progress based on voluntary commitments, there are still gaps across the EU, notably in terms of national capabilities, coordination in case of incidents spanning across borders, and in terms of private sector involvement and preparedness. In terms of airports in the EU, they are specifically vulnerable because air transport infrastructure (that includes ground and inflight ATM) is dependent on continuous and uninterrupted information flows and databases, which cannot be allowed to fail. An agreement on a Directive on NIS is planned for the end of 2014.
What is more, the UK Centre for the Protection of National Infrastructure (CPNI) published a report in 2012, Cyber-security in Civil Aviation, based on discussions of the Joint Coordination Group (JCG), which states that cyber-security should be part of all civil aviation considerations. The JCG aims to coordinate operations related to developing cyber-security for the air transport industry. The report gives a background of the current situation, and names organisations and government bodies that are related and involved with the issues. Furthermore, it gives recommendations and guidance that the aviation industry should consider, in order to increase its cyber-security.
Research: ECAC Study Group & the EACCC
Furthermore, the European Civil Aviation Conference (ECAC) has a Study Group on Cyber Threats to Civil Aviation that provides guidance for Member States, in terms of cyber-security control measures. The Study Group considers recent developments in cyber-security and a cyber-threat matrix taking into account work that was done by the International Civil Aviation Organisation, a framework for establishing best practices for reducing cyber-attacks on critical aviation information systems (CIAS), and risk assessment comparability.
Conclusions and lessons learned were presented from a cyber-crisis management exercise, which was held in May 2013 and one of the aims was to activate the European Aviation Crisis Co-ordination Cell (EACCC). The guidance material, written by the Study Group, is a supplementing directive on ‘cyber-threats to aviation’ in ECAC DOC30 chapter 14.
When the guidance material is prepared and published, it will depend on Member States to ensure that organisations and air transport operators take actions and implement measures accordingly. Although the guidance material is more focused on Air Traffic Management (ATM) and aircraft systems, airports are also encouraged to take action. ACI EUROPE has two representatives (from Birmingham Airport and ADP) in the ECAC Study Group and is actively involved in this work.
If we look at the US, the Transportation Research Board (TRB) is a part of the National Academies of Science that is aiming to develop Airport Cyber-security Best Practices. The research team, which consists of Grafton Technologies, Embry-Riddle Aeronautical University, Massport, or Grafton Information Services, asks airports to share their experience, knowledge and concerns about cyber-security issues. The results of this research will be freely available in a guidebook and multi-media material on the TRB website. The outcome of this research is intended to help airports to set up and manage an efficient cyber-security programme.
How airports can prepare
There are a number of actions that airports could consider and implement in order to protect their business. Firstly, it is important to recognise the cyber-risk and threat, and then it would be easier to establish a cyber-security strategy, objectives, vision, and mission.
Secondly, promotion of cyber-security awareness would be effective at all levels, both business practices and the interface with customers. In particular, industries should reflect on ways to make CEOs and Boards more accountable for ensuring adequate cyber-security measures.
The first step could be the provision of training on cyber-security to all relevant staff, and a dialogue at all levels of airport management. Furthermore, airports should regularly test their own systems through the use of external audits, penetration testing, and regular examination of the airport’s websites. What could also help is deployment of advanced protection gateways for Supervisory Control And Data Acquisition (SCADA) networks. SCADA is a part of airports’ critical infrastructure and responsible for control of equipment (water pipes, apron services, etc), and having security devices installed, would eliminate the risk of access by cyber criminals to SCADA networks.
Moreover, airports should be encouraged to share their experience with other airports and national and international organisations by spreading the word through conferences, meetings, and so on.
ACI EUROPE is following discussions in the Council and European Parliament to ensure that the interests of airports are taken into account and that any reporting requirements are not too burdensome for members.
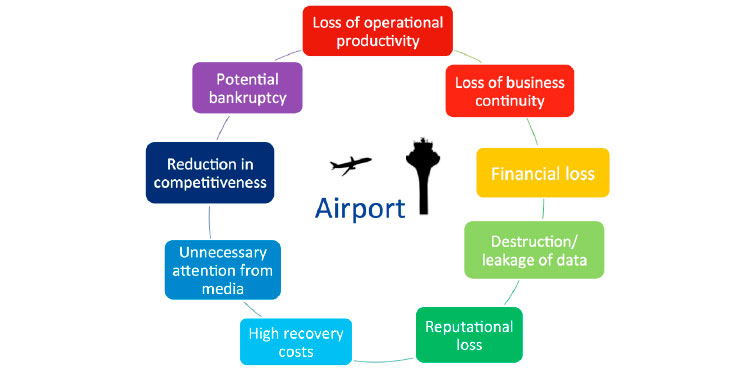
It is crucial to understand that the disruption caused by a cyber-attack also depends on the airport’s size and traffic. However, all these types of incidents may result in long-term implications, such as those pictured, for any type of airport.
Not just for geeks
Ostensibly, cyber-attacks are not the responsibility of IT departments alone; it covers all the elements of an airport business and should be considered as a serious threat. Since airports are heavily dependent on interconnected systems, a sudden shutdown or a failure would undoubtedly reduce and suspend the continuity of business for an indefinite amount of time.
There is absolutely no guarantee that cyber-attacks will not happen, but if – or rather when – they happen, the time it takes to recognise, analyse and respond to an incident will limit the damage and lower the cost of recovery to an airport. The consequences can cost billions, but it is not only about the money: trust and reputation of the airport would be significantly harmed as well. Possible next step? “Put Cyber-security on the agenda before it becomes the agenda” (UK GCHQ, 2012).







